Cuprins
- Abstract 2
- Title: System Security Assessment using Vulnerability Repositories 1
- Chapter 1: Introduction 1
- Background of the research 1
- Problem statement 1
- Research aim 2
- Research Objectives 2
- Research Questions 2
- Statement of Hypothesis 2
- Rationale of the study 2
- Significance of the study 3
- Route map of research 3
- Chapter 2: Literature Review 6
- Project Plan 11
- Chapter 3: Research Methodology 13
- Chapter 4: Findings and Analysis 22
- References 37
Extras din proiect
Abstract
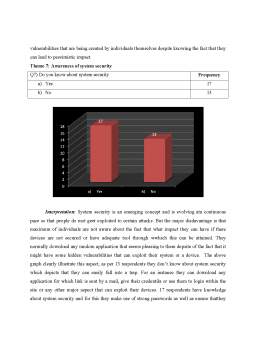
System security illustrates the protection of system from unwanted and unauthorised access. This denotes that system is vulnerable to attack if it is not handled in an effectual manner and appropriate measures are not being taken. The software applications along with operating systems are exploitable to vulnerabilities like SQL injection and various others which already exist. System security illustrates the method which can be utilised by individuals or organisation for securing their assets. For an instance, firewall is utilised for improvising security. In this rules are formulated for filtering unwanted intrusions so that they do not get access to the system and carry out any kind of harmful activities. Thus, there is a need of a tool through whose assistance these vulnerabilities can be measured and their likeability can be minimised.
Title: System Security Assessment using Vulnerability Repositories
Chapter 1: Introduction
Operating system is liable for controlling access to resources that comprises of sensitive data. This implies control of access to resources of computer systems that involves data as well as operating system files. This is referred to as system security (Fu and et. al, 2019). Security vulnerability illustrates the weakness of an adversary which can be taken advantage off to compromise with availability, confidentiality along with integrity of resources. As the technology is evolving, there is enhanced probability to enter within them. The operating system and software apps have become exploitable to the system vulnerabilities which to leads to security concerns. Vulnerability denotes weakness that may be exploited via threat actor like attacker carrying out unauthorised actions in computer system. Basically, it implies cyber security term that illustrates flaw within system, which leads to creation of open attack. They signify weakness of computer system that comprises of procedures or anything that leads to expose information security. For this it is necessary for identification of applications which have vulnerabilities and can lead to have worst impact on individuals system. This will lead to identify vulnerability that might be prevented to from attacking as well as having access to data.
Background of the research
Computer vulnerability refers to cyber security term that denotes defect within a system that makes it prone to attacks. This signifies type of weakness which is present within computer system or mobile phones that comprises of set of procedures or aspects that lead to aid information security by which this can be exposed to threat. This can lead individuals to have various problems like threat of leakage of their private information (Bhatia, Christopher and Thangapandian, 2020). In case if firm’s network is being exposed or mobile device of any employee is accessed by intruder then they can have credential information of them which can be utilised against then. Even identity theft can be used to have access to wide range of data.
Problem statement
Operating system implies software which interacts with hardware as well as aids other programs to execute. This involves fundamental files or system software that is required by computers along with mobile phones requires OS to boot up and carry out their functionalities (Casola and et .al, 2020). Behind this lots of programming is involved in different languages basically, it is Java, C and many more languages which allows firms as well as individuals to carry out their operations in smooth manner. This leads to certain vulnerabilities that pose threat to these devices as there is a probability that program might have skipped certain aspects which makes them vulnerable. This means that there is a need for an application that will lead to identify these vulnerable apps which will lead to hamper the functionalities of operations or information stored within them (Chen and et. al, 2020).
Research aim
“To identify the system security assessment through the usage of vulnerability repositories”
Research Objectives
- To identify the concept of system security along with vulnerabilities present within.
- To identify the impact of existing software vulnerability upon apps as well as operating system.
- To analyse the effectiveness of creating a new tool in order to reduce the risk of system vulnerability.
Research Questions
- Illustrate concept of system security along with vulnerabilities within them.
- Identify the impact of existing software vulnerability upon apps as well as operating system.
- Conduct analysis of effectiveness of creating a new tool in order to reduce the risk of system vulnerability.
Statement of Hypothesis
H0: New tool for system security will lead to have affirmative reduction of risks associated with system vulnerabilities.
H1: New tool for system security will not have any influence on reducing risks related with system vulnerabilities.
Bibliografie
Books & Journals
Bhatia, A., Christopher, S. and Thangapandian, W., American Megatrends Inc, 2020. Auto detection mechanism of vulnerabilities for security updates. U.S. Patent Application 16/171,541.
Casola, V. and et .al, 2020. A Novel Security-by-Design Methodology: Modeling and Assessing Security with a Quantitative Approach. Systems and Software, 1(1), pp.1-13.
Chen, J. and et. al, 2020. An Automatic Software Vulnerability Classification Framework Using Term Frequency-Inverse Gravity Moment and Feature Selection. Journal of Systems and Software, p.110616.
Choudhary, S. and et. al, 2020. Proposed Data Structure for Storage of Metrics Values: Misuse Case Oriented Quality Requirements (MCOQR) Framework Perspective. In Performance Management of Integrated Systems and its Applications in Software Engineering (pp. 211-215). Springer, Singapore.
Conklin, W.A. and et. al, 2015. Principles of computer security. McGraw-Hill Education Group.
Dorsey, L.C. and et. al, 2020. Self healing databases for predictive risk analytics in safety-critical systems. Journal of Loss Prevention in the Process Industries, 63, p.104014.
Dotson, J. and et. al, Whistic Inc, 2020. Methods and systems of assessing and managing information security risks in a computer system. U.S. Patent 10,592,675.
Eghan, E.E. and et. al, 2020. The missing link- A semantic web based approach for integrating screencasts with security advisories. Information and Software Technology, 117, p.106197.
Fisch, E. A., White, G. B. and Pooch, U.W., 2017. Computer system and network security. CRC press.
Fu and et. al, 2019. Research on joint optimal dispatching method for hybrid power system considering system security. Applied energy, 238, pp.147-163.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on modern cryptographic solutions for computer and cyber security. IGI global.
Holz, E.A. and et. al, International Business Machines Corp, 2020. Amalgamating code vulnerabilities across projects. U.S. Patent 10,621,361.
HUANG, T. And et. al, 2020. CHALLENGES AND NECES CHALLENGES AND NECESSITIES OF VULNERABILITY VULNERABILITY ASSESSMENT ASSESSMENT FOR POWER SYSTEMS POWER SYSTEMS POWER SYSTEMS INFRASTRUCTU INFRASTRUCTU INFRASTRUCTURES.
Kelley, S.H., Jain, A.S.C. and Turner, S., Airwatch LLC, 2020. Detecting vulnerabilities in managed client devices. U.S. Patent Application 16/600,986.
Kudjo, P.K. and et. al, 2020. The effect of Bellwether analysis on software vulnerability severity prediction models. Software Quality Journal, pp.1-34.
Lever, K.E. and Kifayat, K., 2020. Identifying and mitigating security risks for secure and robust NGI networks. Sustainable Cities and Society, p.102098.
Li, D., Assured Enterprises Inc, 2020. Method and system for identification of security vulnerabilities. U.S. Patent 10,528,745.
Luh, R. and et. al, 2020. PenQuest: a gamified attacker/defender meta model for cyber security assessment and education. Journal of Computer Virology and Hacking Techniques, 16(1), pp.19-61.
Preview document
Conținut arhivă zip
- Computer security.doc